Penetration Testing
Uncover The Power of Penetration Testing for the Best Security
Building Stronger Cybersecurity by Testing and Using Smart Solutions
Improve Your Security with Our Trusted Penetration Testing Services.
Vulnerability Assessment and Penetration Testing
At ByteGRC, we offer thorough vulnerability assessments and penetration testing services to help keep your data and systems safe. Our security experts work with you to find potential weaknesses and recommend effective ways to reduce risks. We also conduct penetration tests that mimic real-world attacks to evaluate how well your organization can detect and respond to threats.
Our experienced team tailors a testing plan to fit your specific environment and business needs, ensuring that all important aspects of your security are reviewed.
We provide various testing services, including black box, white box, social engineering, and physical security assessments. This comprehensive approach helps us find any vulnerabilities that could put your organization at risk.
Don’t wait until it’s too late—contact ByteGRC today to learn more about our penetration testing services and how we can improve your business’s security.
Ethical Hacking to Prevent Potential Intrusions
ByteGRC offers comprehensive penetration testing services to uncover system vulnerabilities, validate existing security measures, and provide a detailed remediation roadmap.
Our team, equipped with the latest tools and industry-specific test scenarios, conducts thorough checks to identify vulnerabilities in systems, applications, services, OS, configurations, and compliance with security policies.
Types of Penetration Testing We Provide
- Network Services Testing
- Web Application Penetration Testing
- Physical Security Testing
- Remote Access Security Testing
- Social Engineering Testing
Penetration Testing Process Deliverables
After we finish the penetration testing, we provide clear reports and practical recommendations to fix any security issues we find.
- Summary of findings and achieved results.
- List of detected vulnerabilities, classified by ease of exploitation and potential impact.
- Summary of changes made during testing.
- Test protocol, including tools used, parts tested, and issues found.
- Actionable recommendations to address revealed security issues.
Mobile Penetration Testing
At ByteGRC, we conduct mobile penetration testing to check for security weaknesses in custom mobile applications for iOS and Android. Our aim is to find vulnerabilities that could lead to data loss or compromise your app’s integrity.
Our experienced testers carefully analyze the traffic between the mobile app and its API. We examine the structure of requests, change fields, and intercept data to protect your application from potential threats

For the mobile application, we test:
- Data storage
- Network communication (API interaction)
- Platform interaction – local identification
- Security configurations (signatures, debugging)
For the API and server, we test:
- All functionalities
- Server services (web, mail, FTP, SSH)
- Security configurations of each component
- Use of third-party components
We carefully record our findings and create a detailed report. This report includes the areas we tested, the vulnerabilities we found, and our recommendations for fixing them. It helps developers address and resolve any issues we discovered.
The report includes:
- Identified flaws
- Locations of flaws
- Descriptions of flaws
- Implications of flaws and potential exploitation
- Exploitation details during testing
- Remediation recommendations
We rate vulnerabilities based on how likely they are to occur and their potential impact. Our team works to fix critical vulnerabilities to improve the security of your mobile application.
Common Mobile Penetration Testing Vulnerabilities:
- Improper Platform Usage
- Insecure Data Storage
- Insecure Communication
- Insecure Authentication
- Insufficient Cryptography
- Insecure Authorization
- Client Code Quality
- Code Tampering
- Reverse Engineering
- Extraneous Functionality
Benefits of Mobile Penetration Testing
- Better Security: Find and fix weaknesses to stop unauthorized access and data breaches.
- Follow Rules: Comply with industry regulations and standards for mobile app security.
- Build User Trust: Protect user data to boost their confidence in your app.
- Manage Risks: Spot and reduce risks before they can be used by bad actors.
- Ongoing Improvement: Regular testing keeps security strong and improves it over time
Mobile penetration testing is a key part of a strong security plan. By finding and fixing potential weaknesses, we help keep your mobile apps secure and ready to handle new threats.
Network Penetration Testing
Network penetration testing helps find weaknesses in your network systems and applications. We use various techniques to check your network’s security and identify potential vulnerabilities before attackers can take advantage of them.
This thorough evaluation allows businesses to understand their network’s security level, test their security measures, prevent breaches, and improve future protection. It is particularly useful for businesses with established security practices or those who believe their defenses are strong.
We provide Black Box and White Box testing services. Our goal is to find security weaknesses that could put your organization at risk.
- Black Box Testing
- White Box Testing
White box testing gives a complete view of how a network works. This method helps you better understand your security measures and find possible weaknesses.
Benefits of Network Penetration Testing
- Understanding your network's normal activity
- Testing how secure your systems are
- Stopping network and data breaches
- Making sure your network and systems are fully secure
API Penetration Testing
API penetration testing involves ethical hacking to check the security of your API design. We test for vulnerabilities and give recommendations to strengthen your API. This helps protect against unauthorized access and potential data breaches.
Our complete API penetration testing services ensure your API endpoints follow best practices. We analyze to confirm that your APIs support your web and mobile applications securely. This testing shows how vulnerabilities could affect your business, including issues with confidentiality, availability, and integrity. Our reports help you prioritize vulnerabilities for quick fixes and manage your budget for better cybersecurity.
We use both manual and automated testing methods. Automated tests are quick, but we think thorough manual testing is crucial for a full evaluation. At ByteGRC, we apply careful manual techniques to make sure our penetration tests are effective and complete.
Benefits of API Penetration Testing
API testing checks the security of your methods and data. Our expert team makes sure that business logic stays intact while safely transferring data between applications and databases.
Regular updates and frequent testing of APIs help keep performance reliable and avoid expensive fixes. Improved API security lowers the risk of data theft and application breaches.
Web Application Penetration Testing
Web application penetration testing simulates attacks on your web applications to evaluate their security. The main goal is to find vulnerabilities that could be exploited by hackers. This process helps assess your applications’ security, identify potential risks, and verify that effective security measures are in place.
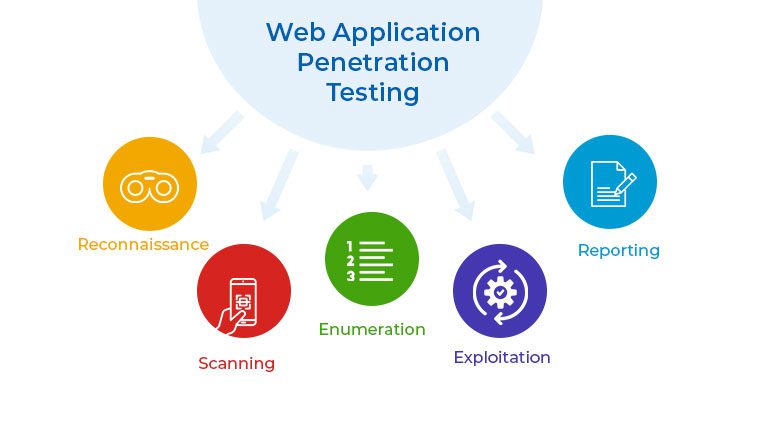
Our testing follows a structured approach for thorough assessments:
1) Planning Phase
In the planning phase, we establish the scope, timeframe, and goals of the testing. We define the target environment and develop communication methods. This phase guarantees that we handle both internal and external testing requirements within a specific period to strengthen your application’s security posture.
2) Pre-Attack Phase
This phase comprises reconnaissance to obtain information that will guide the succeeding testing stages. We execute duties such as port scanning and vulnerability assessment to uncover possible security issues.
3) Attack Phase
During the assault phase, we undertake vulnerability identification and exploitation based on the results from the preceding phase. Our purpose is to imitate real-world assaults to evaluate the efficiency of your security solutions.
4) Post-Attack Phase
After finishing the testing, we deliver a full report including vulnerabilities, analysis, and suggested actions. This report contains a full review of our findings and recommendations for increasing your security.
Benefits of Web Application Penetration Testing
Adding web application penetration testing to your security plan has important benefits:
- It helps you meet compliance requirements, ensuring you follow industry standards.
- It checks your systems for potential weaknesses in public-facing applications.
- It finds critical vulnerabilities that could be exploited, improving your application security.
- It tests your security policies to see how well they protect against threats.
Deliverables
Upon completion of the penetration test, we provide a detailed report with actionable recommendations to address identified vulnerabilities:
- A list of found security weaknesses, sorted by how serious they are and their potential effects.
- A record of any changes made during testing
- The testing process, including the tools and methods used.
- Practical advice on how to fix the identified security problems.
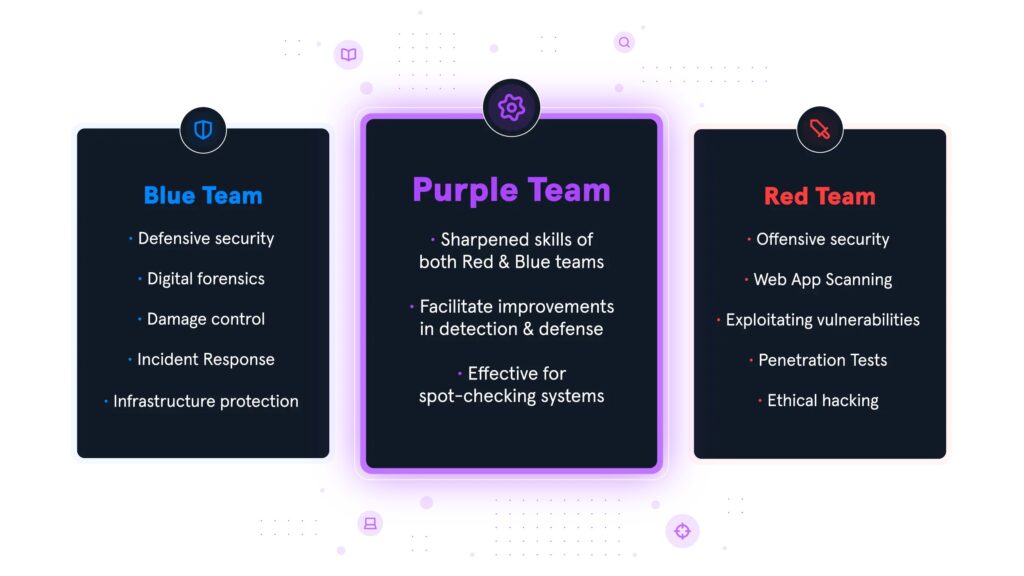
Red Team
At ByteGRC, our Red Team experts simulate real-world attacks to boost your organization’s security. We find and exploit vulnerabilities in a safe setting to help strengthen your defenses.
Our skilled professionals create realistic attack scenarios using advanced tools. They focus on uncovering weaknesses in your infrastructure, processes, and personnel.

This practice, known as “ethical hacking,” tests your organization’s security by mimicking actual attackers. It helps you evaluate how well your defenses stand up to real threats.
Our exercises address not only technical issues, but also human and physical factors. We use techniques like social engineering and phishing simulations. The process begins with a thorough reconnaissance phase to gather intelligence and develop an effective attack strategy.
- Clearly define security roles and responsibilities in your organization
- Maintain a security approach that focuses on risks to ensure business continuity.
- Plan and carry out strategies to fix security issues effectively.
- Set up security measures based on how critical and sensitive your data is.
- Report any information security incidents to the right authorities.
Benefits of Red Team Engagement
- Find ways that attackers could get into your system.
- Show how an attacker might move through your system once they gain access.
- Evaluate how well your organization can detect, prevent, and respond to serious threats.
- Consider different outcomes and responses to possible attacks.
- Focus on fixing the highest risks first.
- Make a strong case for improving security and investing in necessary upgrades.
Final Results
We provide a clear report on the results and technical findings from our Red Team exercises. This report includes a complete list of identified vulnerabilities, organized by how easy they are to exploit and their potential impact on your business.
Purple Team
At ByteGRC, our Purple Team services provide a complete approach to cybersecurity by combining offensive and defensive strategies. We connect Red and Blue Teams to help keep your organization’s assets secure.
Our Purple Team enhances the work of the Red and Blue Teams by serving as a feedback bridge. We encourage the sharing of information and real-time feedback, which helps improve your overall security.
Best Practices for Implementing a Purple Team
To get the most from your Purple Team services, follow these best practices:
Define Clear Roles
Make sure everyone knows their roles and responsibilities. Good teamwork and communication are key. Don’t expect Red Team members to manage all vulnerability tasks, and don’t hold Blue Team members to the same standards as expert hackers.
Prioritize Planning
Set clear goals for your Purple Team exercise. Whether you’re aiming to improve security alerts, sharpen policies, or check how employees respond to social engineering, planning is very important.
Track and Revise
Before making any security updates, carefully track and review each step. Assess each task before moving on, and always follow up to ensure everything is thorough.
Purple Team’s Benefits
- Improve how we find vulnerabilities.
- Build a stronger cybersecurity culture by combining Red and Blue Teams.
- Make security designs and training more effective.
Our skilled Purple Team members are well-trained and experienced. They consistently achieve successful results for our clients.
Wireless Security Testing
Wireless Security Testing is crucial for checking how well your wireless networks and devices are set up and working. Our main goal is to make sure that only authorized users can access your network and its services.
We perform detailed wireless assessments by scanning signals and reviewing the configuration of your wireless setup. This helps us find and fix any vulnerabilities that are specific to your system. Since each testing situation is unique, we offer customized solutions instead of fixed-price options.
We will carefully outline your project requirements, estimate the time needed, and give you a detailed proposal that includes a cost breakdown and options.
Our experienced team has years of expertise in both government and commercial sectors, and we always strive to meet your needs.
Wireless Security Testing Methodology
Our wireless testing process has five important steps that help us find and fix security issues.
Information Gathering
In this step, we look for network details and identify the Wi-Fi network names (SSIDs) within range.
Threat Modeling
We analyze the information we gathered to identify potential threats and categorize the assets based on risk.
Vulnerability Analysis
Here, we review and document any vulnerabilities we found in earlier steps.
Exploitation
In this phase, we try to access your wireless network and possibly your internal network by bypassing security measures and testing vulnerabilities to see how they could impact you.
Reporting
Finally, we give you a detailed report with clear findings, risk ratings, and evidence to help you address any issues.
Wireless Security Testing Offers Assurance by Addressing
Access Control
Ensuring your wireless network is protected from external access.
Network Separation
Preventing guest or public hotspot users from accessing internal networks.
Configuration Security
Verifying that access points, controllers, and devices are securely configured.
Deployment Integrity
Ensuring that only authorized access points are installed, with no rogue devices present
