Assessments
A Comprehensive Approach to Data Privacy Evaluation
Assessments
Ensuring Compliance and Security Measures
Data Privacy Assessments & Audit
Data privacy entails preserving personal information by restricting who may access and use it. It’s vital for securing people and companies against identity theft, fraud, and abuse.
Organizations need to secure their employees’ and customers’ personal information. A data privacy evaluation helps estimate how successfully a business is preserving this information.
Common Data Privacy Legislation
- The General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
Sticking to these standards is vital for securing personal information.
Steps for a Data Privacy Evaluation
- Comprehending relevant rules
- Identifying gathered personal information
- Analyzing protective mechanisms
- Examining the incident response plan
The ByteGRC team of certified consultants can assist with data privacy assessments, utilizing our knowledge of GDPR, HIPAA, and PCI DSS to boost your security procedures.

Threat Vulnerability & Risk Assessment
Threat vulnerability and risk assessments serve a critical role in detecting, assessing, and managing hazards connected with information resources. The main purpose is to secure your organization’s information and its stakeholders against possible dangers.
Evaluation Process
The evaluation process usually comprises many critical elements which include:
- Detecting possible dangers
- Assessing their expected effect
- Reviewing current controls
- Suggesting new preventive measures where required.
Different approaches may be applied for these evaluations, such as
- NIST Special Publication 800-30
- ISO/IEC 27005
- COBIT 5
Each of these frameworks has its own strengths; therefore, it is vital to pick the one that corresponds best with your organization’s unique goals.
Information security risk management usually comprises three key phases:
- Assessment
- Response
- Monitoring
For enterprises wanting help with threat and risk assessments, the ByteGRC team is ready to give support. Our professionals apply the latest technologies and strategies to provide a complete and successful protection plan for your firm.
Compromise Assessments
A compromise assessment is a critical technique for detecting and controlling the risks associated with prospective cyber-attacks. Its major purpose is to deliver actionable insights that increase the security of systems and data.
These examinations may be categorized into two primary categories: technical and non-technical. Technical assessments concentrate on analyzing system configurations and current security procedures, while non-technical assessments focus on organizational and administrative issues that may affect cybersecurity.
There are different forms of compromise evaluations, including:
- Technical Assessments
- Non-Technical Assessments
ByteGRC delivers extensive compromise assessments meant to assist businesses in uncovering vulnerabilities and preparing for possible security crises. Our experienced counsel and assistance seek to increase your organization’s defenses against cyberattacks.
Cloud Security Assessments
A cloud security assessment is a rigorous study of your cloud environment’s security posture. This approach entails a thorough study of your cloud provider’s security standards, a full assessment of how your business interacts with the cloud, and a comprehensive grasp of how you intend to exploit cloud capabilities.
Whether you’re planning a transfer to the cloud or are currently employing different cloud services, these evaluations are essential in highlighting possible risks and weaknesses. They also play a significant role in creating strong solutions to successfully reduce such risks.
Key Phases in Managing Cloud Security Risks:
- Migrating data or apps to the cloud
- Implementing additional cloud features or functionalities
- Transitioning to a different cloud provider
- Adding additional users or groups to your cloud environment
Assessments might be undertaken by your own teams or by skilled external specialists. When hiring an assessor, emphasize their experience, knowledge, and comprehensive grasp of your unique security requirements. After the evaluation, it’s necessary to methodically evaluate the data and establish a strategy plan to manage any identified risks. Regularly updating this strategy is crucial for keeping a good cloud security architecture.
At ByteGRC, we specialize in discovering and analyzing your cloud security vulnerabilities. Reach out to us to learn how our cloud security assessment services can enhance your organization’s defenses and guarantee a flawless cloud experience.

Vulnerability Assessments
Vulnerability assessment is a crucial process that systematically uncovers security weaknesses within your computer networks, hardware, applications, and systems. By undertaking these assessments proactively, you can identify and mitigate risks before they escalate into significant threats. At ByteGRC, our experts deliver meticulous and tailored vulnerability assessments designed to align with your specific needs.
Our comprehensive vulnerability assessments not only identify and prioritize weaknesses but also provide a clear and actionable roadmap for remediation.
Our Assessment Process
- Defining and Planning the Scope of Testing: We start by carefully defining and planning the parameters of the assessment to ensure a focused approach.
- Identifying Sensitive Data Locations: Our team meticulously locates sensitive data to shield it from potential threats.
- Uncovering Hidden Data Sources: We dig deep to uncover hidden data repositories that may pose risks.
- Identifying Mission-Critical Applications: We pinpoint applications that are vital to your operations, ensuring they receive priority attention.
- Assessing Network and System Access Points: Our evaluations of access points help strengthen your defenses against unauthorized entry.
- Reviewing Ports, Processes, and Configurations: We conduct thorough reviews to identify potential vulnerabilities in your system’s architecture.
- Mapping Out IT Infrastructure and Digital Assets: Our detailed mapping of your IT assets allows for a comprehensive assessment of risk exposure.
The Assessment Phases
- Defining and Planning: We lay the groundwork for a thorough assessment tailored to your unique environment.
- Vulnerability Identification: Through a combination of advanced scans and manual testing, we unveil potential threats.
- Analysis: Our team analyzes findings, prioritizing vulnerabilities based on risk severity, and formulates a detailed remediation plan.
- Remediation: We help you implement effective fixes based on the remediation plan, safeguarding your systems and preventing future exploitation.
For thorough vulnerability assessments and impactful remediation strategies, connect with ByteGRC today and take the first step towards fortifying your security posture.
Social Engineering Assessments
Social engineering assessments test how well your employees respond to security threats. These tests simulate real-life situations where attackers use common human traits, like trust and emotional reactions, to gain unauthorized access to sensitive information.
We use psychological tactics to trick people into actions like clicking on fake links, opening harmful attachments, or sharing private details. This helps us see how well your team handles such manipulation and how effective your current security measures are.
A successful social engineering attack can seriously harm your business, putting critical data and employee information at risk. ByteGRC’s social engineering services check how well your systems and staff detect and respond to these attacks. We carefully plan the tests with you to ensure they are controlled and provide valuable insights. Our assessments help identify:
- Risks from employee actions that could cause sensitive information leaks.
- Awareness of your organization’s online presence and how much public information is available.
- Effectiveness of tHow well technical controls can find and respond to social engineering attacks.echnical controls in detecting and responding to social engineering attacks
- Areas where employees lack cybersecurity awareness.
- Suggestions for improving employee behavior and sensitivity to cybersecurity issues.
Our Social Engineering Services Include
- Voice Phishing: Targeted phone-based social engineering campaigns
- SMS Phishing: Targeted SMS-based social engineering campaigns
- Tailgating: Gaining access to restricted areas by following employees
- Chat Phishing: Using messaging/chat services for social engineering
- Physical Bypass: Techniques to gain physical entry to secure areas

Our Methodology
Our social engineering assessment process includes:
- Information gathering and OSINT
- Target profiling and finalizing attack mode
- Launching the test
- Analyzing test results
- Reporting

Our Benchmarks
Our assessments meet the user awareness evaluation and training requirements for benchmarks like:
- ISO 27001:2013
- PCI-DSS
- Cybersecurity guidelines from regulatory authorities
Why Choose Us?
- We have a lot of experience assessing businesses in various fields.
- Our highly trained team tailors their approach to meet each client's needs
- We provide detailed reports that explain test results and their impact on the business.
- We also design long-term campaigns to enhance information security awareness within the organization.
Cyber Security Maturity Assessments
The Cyber Security Maturity Assessment (CSMA) gives a thorough perspective of your existing security posture. It gives an impartial analysis of current strategies and supports strategic planning to mature and enhance your security efforts. Aligning your security program with the best practices highlighted in this evaluation boosts your capacity to meet and exceed industry compliance requirements.
HOW IT WORKS?
The CSMA assesses particular policies that safeguard vital assets, infrastructure, applications, and data by analyzing your organization’s defensive posture. It outlines operational best practices for each control area and assesses the efficacy and maturity of internal rules and procedures.
The audit also involves an examination of compliance with numerous industry regulations and guidelines, including:
- Center for Internet Security Top 20 Common Security Controls (CSC20)
- NIST Cybersecurity Framework (NIST CSF)
- NIST Special Publication 800-53 (NIST 800-53)
- NIST Special Publication 800-171 (NIST 800-171)
- Department of Energy Cybersecurity Capability Maturity Model (DOE-C2M2)
- ISO/IEC 27001:2013 (ISO 27001)
These frameworks give a formal way to assess the maturity and efficacy of your security program, both now and in the future.
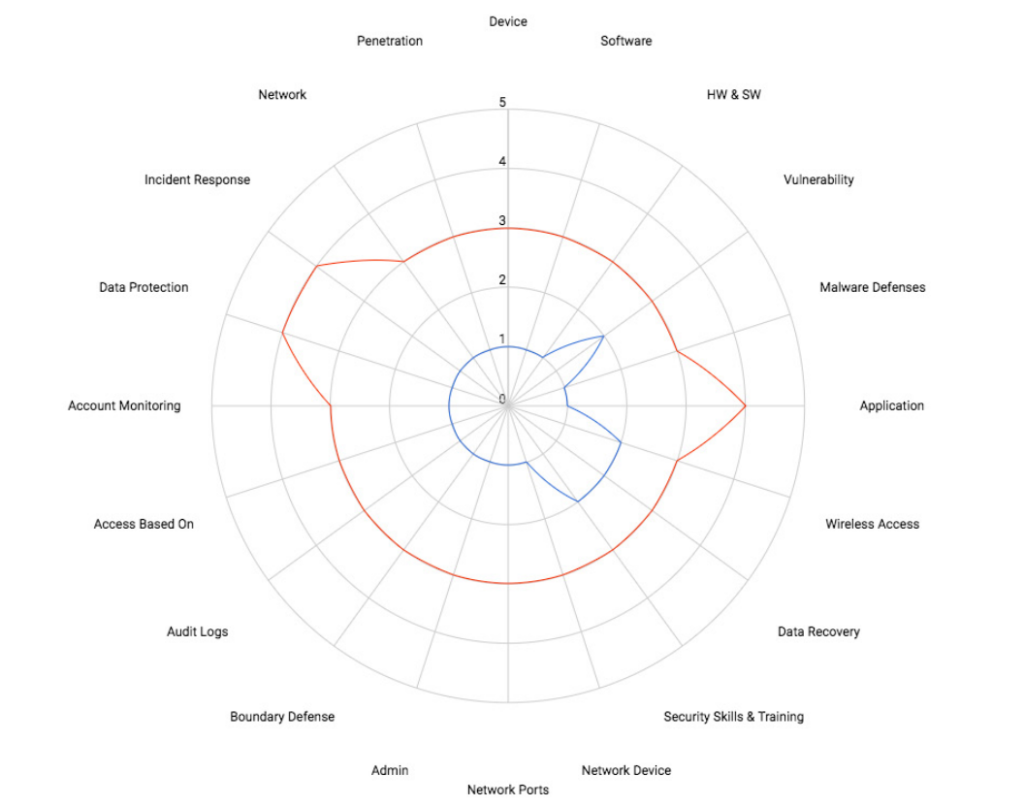
The Capability Maturity Model

PCI DSS:
ByteGRC helps businesses follow the Payment Card Industry Data Security Standard (PCI DSS), which is a global security rule to protect debit and credit card information. If your business handles card payments, you need to meet PCI DSS rules to prevent fraud and keep transactions secure.
PCI DSS was created by major card companies like American Express, Discover, JCB, Mastercard, and Visa. These companies work together under the Payment Card Industry Security Standards Council (PCI SSC) to monitor and enforce these rules.
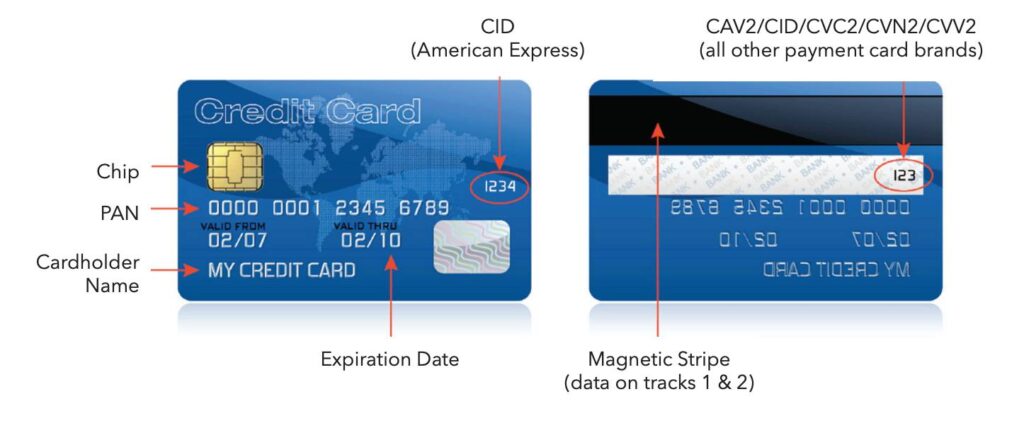
As a certified Qualified Security Assessor (QSA), ByteGRC offers a wide range of services to help businesses meet all PCI DSS requirements and stay compliant. We guide our clients through the whole process to make sure they follow all the rules and protect their customers’ data.
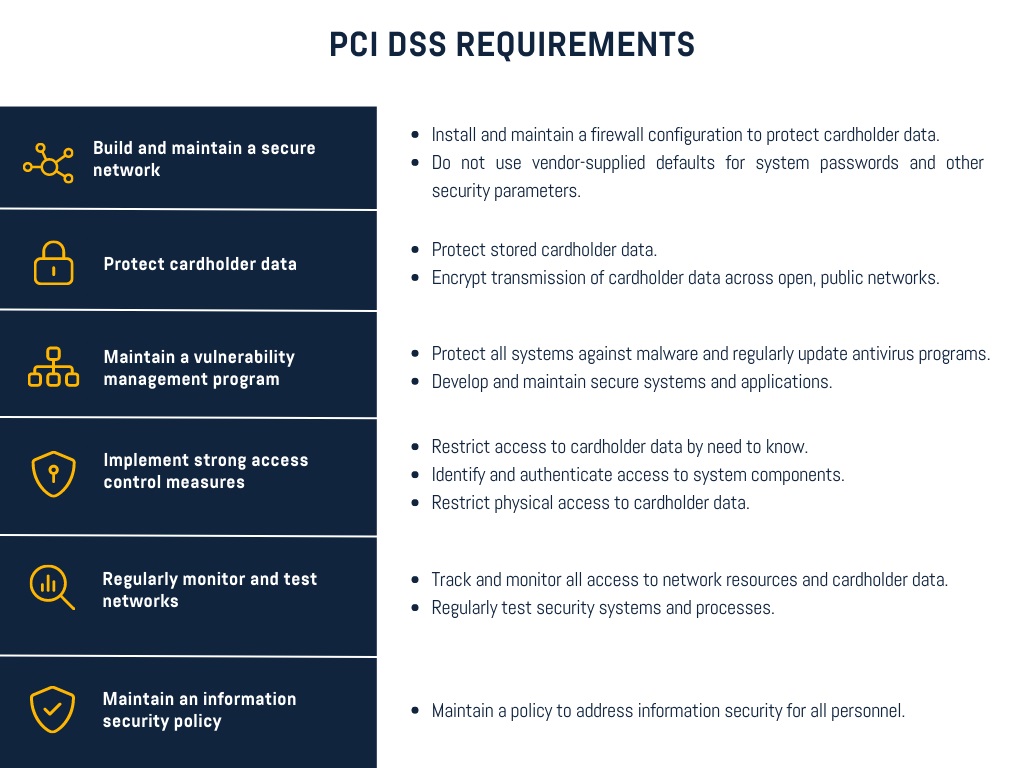
PCI DSS has 6 main goals and 12 specific requirements that every business handling card payments must follow. These rules cover security systems, processes, and testing, and are designed to protect cardholder information. Meeting these requirements means following detailed rules that focus on keeping data safe.
Our experienced team at ByteGRC helps businesses understand and meet all the PCI DSS requirements to get certified and stay protected.
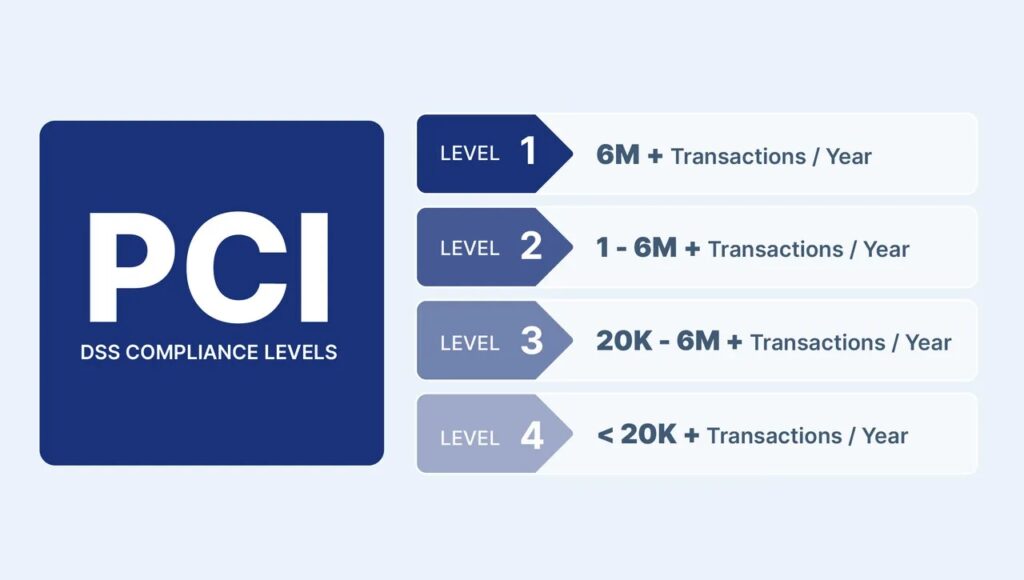
Our experts also help businesses prevent data breaches and fraud. We provide professional guidance on the right PCI DSS level for each business, depending on how many card transactions they handle each year.
Benefits of PCI DSS Certification
- Builds customer trust
- Helps avoid penalties
- Reduces security risks
- Meets other industry standards
